Developing, marketing, and making an application successful in this competitive market is a challenging task. Along with this when your application is a platform and it is accessible to multiple users, that tie data privacy and protection is very important as well as difficult to maintain.
An application that needs to be secured, is straightforward to hack. One with the capability to perform the following tasks can easily penetrate the application database and misuse it:
- Knowledge of data access from application storage
- Access the app database passcodes
- Trace the digital footprints of data and credentials
- Reverse-engineering a spoof mobile application
- Inject malware into the application
- Steal intellectual property and private business assets
Hire mobile app developers who have to pay attention to eliminating security risks during development by improving the security systems of the mobile application. Being a developer or a business looking for the Best app development services, this blog will be very helpful to every reader looking for the best assistance in cyber security.
Why Mobile Application Security is Important?
vulnerabilities to security threats and breaches are increasing each day over the internet. As businesses and consumers are shifting to the online platform, cybercrime is making its space in the sensitive parts of it. Data and infrastructure available ver the multiple networks can be easily accessed and moderated for misuse. Application security testing can reveal weaknesses at the application level, and help mobile app developers to prevent these attacks.
Types of Mobile Application Security
Multiple ways of mobile app security include login & signup authorization, authentication, security testing, and encryption. Mobile app developers can code mobile apps from the initial stage reducing vulnerabilities.
Authentication:
Hire mobile app developers, who build Multi-factor authentication that requires more than one form of authentication—the factors might include something you know (a password), something you are (a thumbprint or facial recognition), and something you have (a mobile device).
Authorization:
After a user has been authenticated, the user may be authorized to access and use the application. The system can validate that a user has permission to access the application by comparing the user’s identity with a list of authorized users. Authentication must happen before authorization so that the application matches only validated user credentials to the authorized user list.
Encryption:
After a user has been authenticated and is using the application, other security measures can protect sensitive data from being seen or even used by a cybercriminal. In cloud-based applications, where traffic containing sensitive data travels between the end user and the cloud, that traffic can be encrypted to keep the data safe.
Login/Signup:
If an application has a security breach, logging can help identify who got access to the data and how. Application log files provide a time-stamped record of which aspects of the application were accessed and by whom.
What are Mobile Application Security Controls?
Application security controls are methods to strengthen an application’s coding-level security, reducing its susceptibility to attackers. The responses of the application to unforeseen inputs that a hacker might use to exploit a hole are often the focus of these controls. An application’s code can be written by a programmer so that the programmer has more control over the results of these unforeseen inputs.
Fuzzing is a sort of application security testing in which developers examine the outcomes of unexpected inputs or values to identify those that cause the program to behave in a way that might expose a security flaw.
What is Mobile App Security Testing?
Application developers perform application security testing to make sure a new or upgraded version of a software application has no security flaws as part of the Best app development services. A security audit can verify that the application complies with a certain set of security requirements. Developers need to make sure that only authorized users may access the program after it passes the audit.
When conducting penetration testing, a mobile app development company adopts the mindset of a cybercriminal and searches for openings in the application. Social engineering or attempting to trick users into granting unauthorized access are both possible components of penetration testing. To find security flaws that might not be visible in states, testers frequently run both authenticated security scans and unauthenticated security scans (as logged-in users).
Also, Read About:- https://nboxoffice.com/top-listed-android-game-development-tools-2023/
Best Mobile App Security Practices
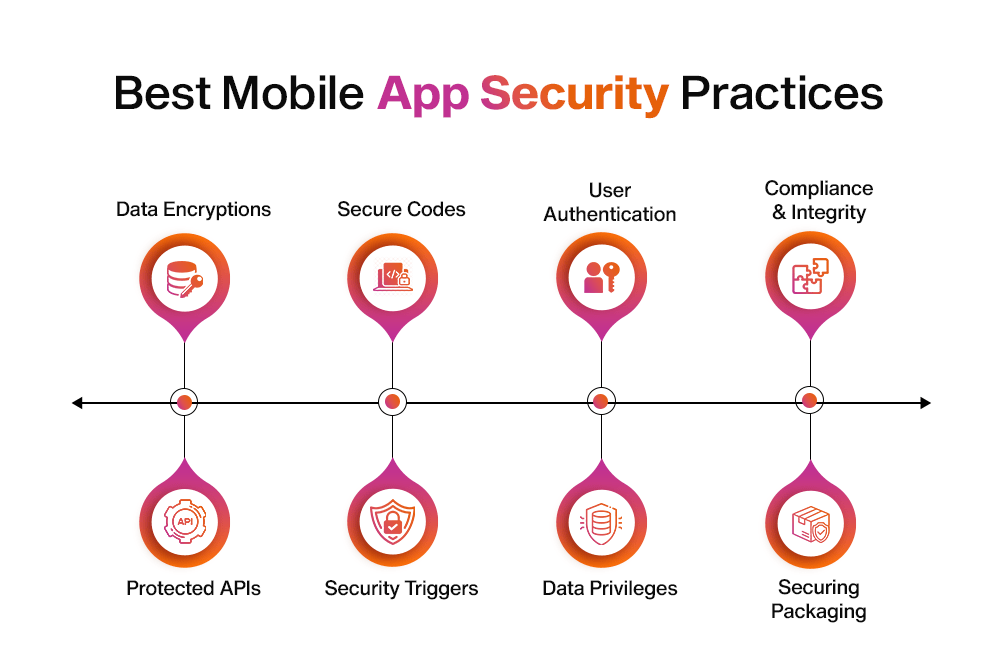
1. Data Encryptions
Numerous consumers use numerous applications across various devices and operating systems. Therefore, you must make sure that no OS or device vulnerability exposes the data transferred over the application.
2. Secure Codes
If you choose a qualified app designer they have mobile app security testing tools, you can rest easy knowing that your app’s security measures are flawless. The easiest way to make sure that the code is secure and that there are no problems that hackers can attack, in addition to having an expert on board, is to test the mobile application.
3. User Authentication
User-generated content (UGC) contributions are most prevalent in mobile applications. Without a suitable user authentication system in place, UGC may be vulnerable to cyberattacks. Hackers can access crucial data.
4. Compliance & Integrity
Any mobile app must meet requirements and pass security checks before it can be deployed. Under the guidance of the app store, there can be particular security precautions that developers must adhere to. These controls may be for an app’s download and installation process.
5. Protected APIs
APIs are necessary for third-party service integration and capability enhancement. It makes it possible for disparate systems to communicate with one another and exchange data. However, you need safe APIs and shouldn’t disclose the data transferred for better app security. The use of data access authorizations is the most effective technique to guarantee API security.
6. Security Triggers
If someone tampers with the application source code, you can use customized triggers to notify your systems. For instance, AWS Lambda functions can be used to guarantee malware injection or app tampering notifications for cloud-native applications.
7. Data Privileges
Finding data privileges is an approach to guarantee that your application is not vulnerable to harmful cyberattacks. When giving limited users access to sensitive data, employ the least privilege technique. This will prevent someone with bad intentions who lacks data access from gaining access to sensitive data.
8. Securing Packaging
You can hire a mobile app development company and use secure containers to store these keys because the majority of organizations employ the hybrid cloud method to keep sensitive data in nearby data centers. As an illustration, you can use enhanced security.
Hire a Mobile App Security Expert
As smartphone usage increases every day, mobile application security should be high on your priority list. Unfortunately, with deceiving attributes and social engineering practices, hackers are getting more efficient at malicious injection attacks.
This means that you need to improve the mobile app security best practices for data security and stop these hackers from taking control of your applications. We hope that these tips are helpful and we’re always happy to guide you along the way!